-
Type:
Bug
-
Status: Closed
-
Priority:
High
-
Resolution: Won't Do
-
Affects Version/s: None
-
Fix Version/s: None
-
Component/s: Integrations
-
Labels:None
-
Bug Type:Functional
-
Module:Platform - Security
-
Reported by:Harbinger
-
Item State:Stage QA - Production Deployment on Hold
-
Issue Importance:Q2
-
Dev Estimates:5
-
Code Reviewed By:Vijayendra Shinde
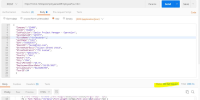
Cross Site Scripting
A Cross-Site Scripting (XSS) Scan attacks clients of the system under test by inserting dynamic code like JavaScript into the input, hoping that the same code is echoed in the response. However, this is only a problem if the response is consumed directly by a browser or if HTML is built in a naive way from the response. In other words, Cross-Site Scripting Scans may sometimes give you false positives.
APIs :
• Show Tours in Company
GET https://stage.workterra.net/api/tours/getTours
• Add Employee and Assign Tour
POST https://stage.workterra.net/api/employee/addEmployeeTour
- Alerts reported :
- Sensitive Information Exposure: null/empty response body
- Cross Site Scripting Detection: null/empty response body
- Cross Site Scripting Detection: Content that is sent in request '<PLAINTEXT>' is exposed in response. Possibility for XSS script attack in: REST Request_GetTourList
Please refer attached report for more details